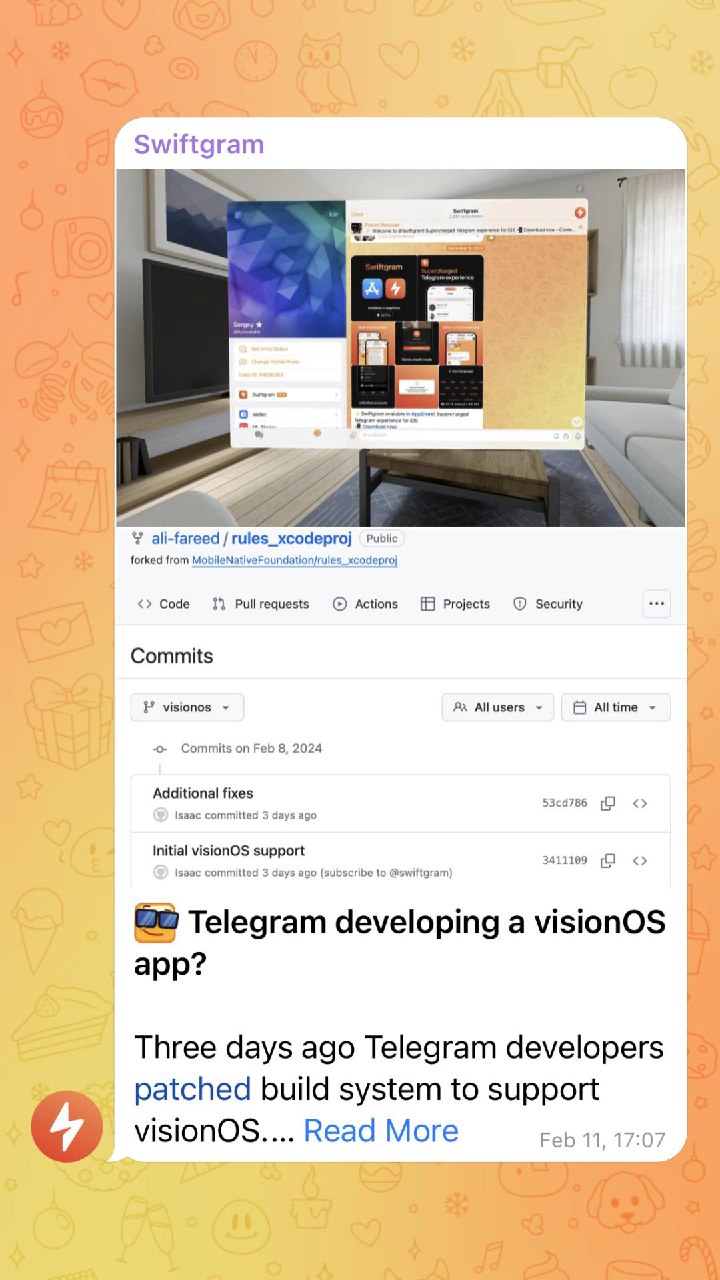
Swiftgram
Supercharged Telegram for iOS
Download - https://apps.apple.com/app/id6471879502
Discuss - @SwiftgramChat
More - @SwiftgramLinks Related channels | Similar channels
15 142
subscribers
Popular in the channel
Next update is delayed. Telegram just released a source code and it’s the first time I can’t upda...
Swiftgram had the same screenshot for both iOS and iPadOS. ✅ iOS Approved ❌ iPadOS Rejected
Update was rejected due to iPad screenshots. I've changed them two months ago.
About Swiftgram Pro Download in App Store Get Pro features tg://sg/pro
Swiftgram Pro FAQ What is Swiftgram Pro? Swiftgram Pro is a paid subscription in iOS app @Swiftg...